As the world becomes increasingly digitized and connected, the importance of regular security log monitoring and response cannot be overstated. In today’s digital age, cyber threats are a constant and growing concern:
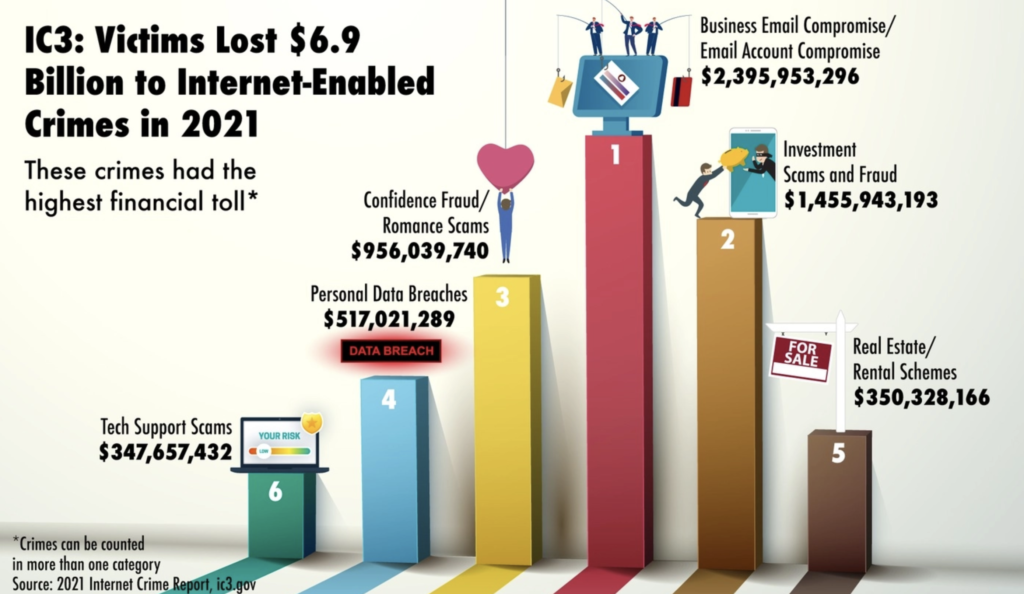
It is essential to have a proactive and comprehensive approach to security. Regular security log monitoring and response is an essential part of any cybersecurity strategy.
One of the key benefits of regular security log monitoring and response is that it allows organizations to detect and respond to potential threats quickly and effectively. By constantly monitoring logs and identifying patterns and anomalies, security teams can quickly identify and respond to potential threats, preventing them from causing significant damage.
According to a study by the Ponemon Institute, organizations that have a strong security incident response plan are able to detect and contain breaches in an average of 46 days, compared to an average of 201 days for organizations without a plan.
Another key benefit of regular security log monitoring and response is that it helps organizations meet compliance requirements. Standards such as ISO 27001 and NIST SP 800-53 require organizations to have a comprehensive security management system that includes regular security log monitoring and response. By implementing these standards, organizations can demonstrate to customers, partners, and regulators that they have taken the necessary steps to protect sensitive data and prevent breaches.
Case studies also demonstrate the value of regular security log monitoring and response:
For example, in 2016, a major healthcare organization experienced a data breach that exposed the personal information of nearly 4 million patients. The cause of the breach was a failure to monitor security logs, which would have revealed suspicious activity and allowed the organization to take action before the breach occurred. This incident highlights the importance of regular security log monitoring and response and the potential consequences of not having it in place.
Companies can do log monitoring in a cost-effective manner by implementing the following strategies:
Automation: Automating log monitoring and analysis can significantly reduce the cost of manual monitoring and analysis. By using automated tools, companies can analyze and identify potential threats in real-time, without the need for manual intervention. This can significantly reduce labor costs and increase the effectiveness of monitoring.
Cloud-based solutions: Utilizing cloud-based log monitoring solutions can help companies reduce the costs associated with maintaining and scaling their own infrastructure. Cloud-based solutions also offer automatic updates, eliminating the need for additional costs to maintain software.
Prioritization: Companies can prioritize their log monitoring efforts by focusing on the most critical systems and applications. This can help them identify and address potential threats more efficiently, reducing costs and increasing the overall effectiveness of monitoring.
Regular testing: Regularly testing and evaluating log monitoring systems can help companies identify potential vulnerabilities and improve their overall security posture. By testing their systems, companies can also ensure that they are able to detect and respond to potential threats effectively.
Outsourcing: Companies can also consider outsourcing log monitoring and analysis to a third-party vendor. This can help them reduce costs associated with hiring and training employees, and also provide them access to specialized expertise and resources.
In addition, companies can also incorporate security ISO and NIST standards into their security log monitoring and response strategy to ensure they are doing it in a cost-effective manner while also staying compliant with the regulations. This will help them manage risks and remain protected from cyber threats.
Remember: regular security log monitoring and response is a critical component of any cybersecurity strategy. By detecting and responding to potential threats quickly and effectively, organizations can prevent significant damage and meet compliance requirements. With the increasing number of cyber threats and data breaches, it is essential for organizations to prioritize regular security log monitoring and response to protect their sensitive information and assets.