
Author: WebMaster
Network Monitoring: Enhancing Cyber Security Operations
In today’s digital landscape, where cyber threats continue to proliferate, ensuring robust security measures is crucial for businesses of all sizes. Cybersecurity operations play a pivotal role in safeguarding sensitive data, mitigating risks, and protecting against potential breaches.
While many organizations focus on implementing firewalls, encryption, and other security measures, one vital but often overlooked step in comprehensive cyber defense is network monitoring. In this article, we delve into the importance of network monitoring in cyber security operations and how it can significantly enhance your organization’s overall security posture.
Understanding Network Monitoring
Network monitoring involves the continuous surveillance of a computer network to identify and respond to security threats, performance issues, and other network-related problems. It provides valuable insights into the overall health, performance, and security of your network infrastructure. By leveraging advanced monitoring tools and technologies, organizations can gain real-time visibility into network activities, identify anomalies, and respond promptly to potential security breaches.
The Vital Role of Network Monitoring in Cyber Security Operations
- Proactive Threat Detection: Network monitoring acts as a proactive defense mechanism, allowing organizations to identify potential threats before they escalate into major security incidents. By monitoring network traffic, suspicious activities, and system logs, IT teams can swiftly detect unauthorized access attempts, malware infections, and other malicious activities. Early detection enables timely response, minimizing the impact of security breaches and preventing sensitive data from falling into the wrong hands.
- Improved Incident Response: In the event of a security incident, network monitoring provides essential data for incident response and forensic investigations. Detailed logs and network activity records enable IT teams to trace the source of the breach, analyze the extent of the damage, and develop effective remediation strategies. This valuable information ensures a more efficient incident response process, reducing downtime and minimizing the potential damage caused by cyber attacks.
- Enhanced Performance Optimization: Network monitoring not only aids in identifying security threats but also offers insights into network performance. By monitoring bandwidth usage, latency, and other network metrics, organizations can optimize their network infrastructure for better performance. Identifying bottlenecks, optimizing traffic flow, and managing network congestion become easier with the continuous monitoring and analysis of network data.
- Compliance and Regulatory Requirements: Many industries are subject to stringent compliance and regulatory standards regarding data privacy and security. Network monitoring plays a vital role in meeting these requirements. By monitoring network activity, organizations can ensure compliance with data protection regulations, identify vulnerabilities, and implement necessary security controls. This proactive approach helps organizations avoid penalties, legal consequences, and reputational damage associated with non-compliance.
- Internal Threat Detection: While external cyber threats are a significant concern, internal threats can also pose a substantial risk to an organization’s security. Network monitoring enables the identification of suspicious activities originating from within the network, such as insider threats or unauthorized access attempts by employees. By monitoring user behavior, access privileges, and data transfers, organizations can detect and mitigate internal security risks more effectively.
Best Practices for Effective Network Monitoring
To harness the full potential of network monitoring, organizations should consider the following best practices:
- Choose the Right Tools: Invest in robust network monitoring tools capable of providing real-time insights into network activities, identifying anomalies, and generating actionable alerts. Select tools that align with your organization’s specific needs and network infrastructure.
- Implement Comprehensive Monitoring: Monitor all critical network components, including routers, switches, firewalls, servers, and endpoints. Ensure that network monitoring covers both internal and external network traffic to gain a holistic view of your organization’s security landscape.
- Continuous Monitoring and Analysis: Network monitoring should be an ongoing process, not a one-time setup. Regularly review network logs, conduct deep packet inspections, and analyze network traffic to identify any
- Outsource the manual portion to WatchDog. Just provide the logs and we do the rest.
The Power of Website Security: Safeguarding Your Online Presence
In today’s digital age, where online interactions have become an integral part of our daily lives, ensuring the security of your website has never been more crucial. Cyber threats and attacks are on the rise, putting sensitive data, user privacy, and even business reputation at risk. As a leading provider of website security solutions, we understand the importance of safeguarding your online presence. In this article, we delve into the realm of website security, offering valuable insights and practical steps to help you fortify your website against potential vulnerabilities and outrank other websites in Google search results.
The Rising Threat Landscape
Cybercriminals are becoming increasingly sophisticated in their methods, constantly seeking new ways to exploit weaknesses in websites. From data breaches and malware infections to hacking attempts and distributed denial-of-service (DDoS) attacks, the threat landscape is diverse and ever-evolving. It is imperative for website owners to adopt a proactive approach to protect their digital assets.
Understanding Website Vulnerabilities
Before we delve into effective security strategies, it is essential to understand the common vulnerabilities that can be exploited by malicious actors. By gaining insights into these weak points, you can take appropriate measures to mitigate potential risks. Here are a few noteworthy vulnerabilities:
1. Outdated Software and Plugins
Running outdated versions of content management systems (CMS) or using obsolete plugins can open doors for cyber attackers. These outdated components often have known vulnerabilities that can be easily exploited.
2. Weak Authentication Mechanisms
Weak passwords, default login credentials, or lack of two-factor authentication (2FA) can leave your website susceptible to brute-force attacks or unauthorized access attempts.
3. Insecure Communication Channels
Failure to implement secure communication protocols, such as SSL/TLS, can expose sensitive data to eavesdropping or interception by malicious individuals.
4. Cross-Site Scripting (XSS)
XSS attacks occur when an attacker injects malicious code into a website, which then gets executed by unsuspecting users’ browsers, potentially compromising their data or exposing them to further attacks.
5. SQL Injection
SQL injection attacks exploit vulnerabilities in web applications that do not properly validate user input. Attackers can manipulate database queries, potentially gaining unauthorized access to sensitive information or modifying data.
Effective Strategies for Website Security
To outrank other websites and establish your online presence as a reliable and secure destination, it is crucial to implement robust security measures. Below, we outline key strategies that will help safeguard your website:
1. Regular Software Updates and Patching
Keeping your CMS, plugins, and other software components up to date is paramount. Developers frequently release security patches and bug fixes to address vulnerabilities. Staying current with these updates is vital to ensure your website remains secure.
2. Strong Authentication Practices
Implementing strong passwords, enforcing password complexity rules, and encouraging the use of 2FA significantly enhance your website’s security posture. By adding an additional layer of verification, you mitigate the risk of unauthorized access.
3. SSL/TLS Encryption
Securing your website with SSL/TLS certificates ensures that data transmitted between your users and the server remains encrypted and cannot be easily intercepted or tampered with. This fosters trust among visitors and can positively impact your search engine rankings.
4. Web Application Firewalls (WAF)
Deploying a WAF helps protect your website against common vulnerabilities, such as XSS and SQL injection. It acts as a shield, analyzing incoming traffic and filtering out potentially malicious requests, ensuring the integrity of your website’s data.
5. Continuous Security Monitoring
Utilize robust security monitoring tools to detect and respond to potential threats in real-time. Implementing intrusion detection systems (IDS)
Cost-Effective Strategies for Log Monitoring and Response: How to Keep Your Company Safe from Cyber Threats
As the world becomes increasingly digitized and connected, the importance of regular security log monitoring and response cannot be overstated. In today’s digital age, cyber threats are a constant and growing concern:
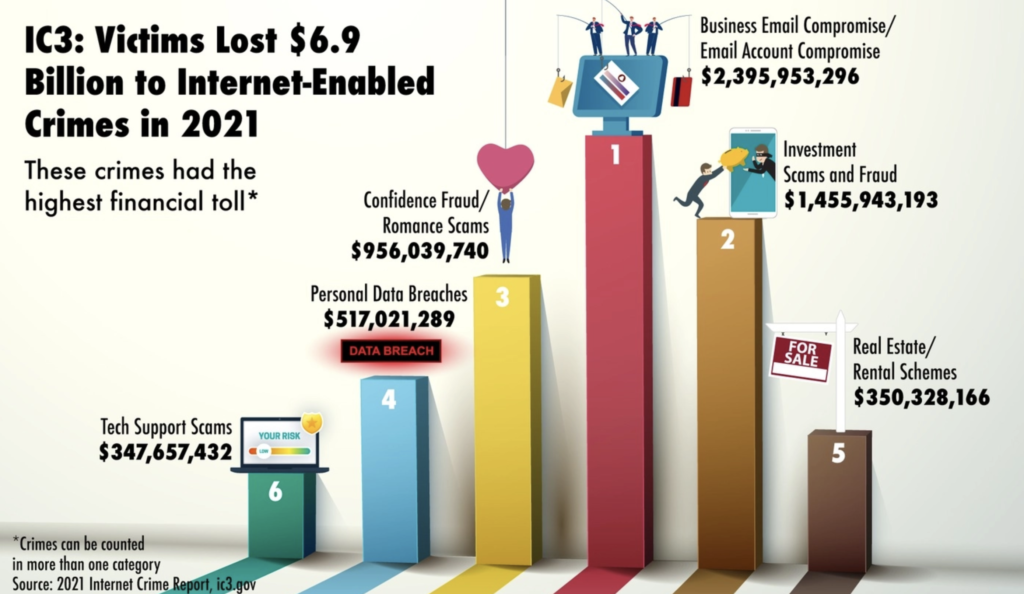
It is essential to have a proactive and comprehensive approach to security. Regular security log monitoring and response is an essential part of any cybersecurity strategy.
One of the key benefits of regular security log monitoring and response is that it allows organizations to detect and respond to potential threats quickly and effectively. By constantly monitoring logs and identifying patterns and anomalies, security teams can quickly identify and respond to potential threats, preventing them from causing significant damage.
According to a study by the Ponemon Institute, organizations that have a strong security incident response plan are able to detect and contain breaches in an average of 46 days, compared to an average of 201 days for organizations without a plan.
Another key benefit of regular security log monitoring and response is that it helps organizations meet compliance requirements. Standards such as ISO 27001 and NIST SP 800-53 require organizations to have a comprehensive security management system that includes regular security log monitoring and response. By implementing these standards, organizations can demonstrate to customers, partners, and regulators that they have taken the necessary steps to protect sensitive data and prevent breaches.
Case studies also demonstrate the value of regular security log monitoring and response:
For example, in 2016, a major healthcare organization experienced a data breach that exposed the personal information of nearly 4 million patients. The cause of the breach was a failure to monitor security logs, which would have revealed suspicious activity and allowed the organization to take action before the breach occurred. This incident highlights the importance of regular security log monitoring and response and the potential consequences of not having it in place.
Companies can do log monitoring in a cost-effective manner by implementing the following strategies:
Automation: Automating log monitoring and analysis can significantly reduce the cost of manual monitoring and analysis. By using automated tools, companies can analyze and identify potential threats in real-time, without the need for manual intervention. This can significantly reduce labor costs and increase the effectiveness of monitoring.
Cloud-based solutions: Utilizing cloud-based log monitoring solutions can help companies reduce the costs associated with maintaining and scaling their own infrastructure. Cloud-based solutions also offer automatic updates, eliminating the need for additional costs to maintain software.
Prioritization: Companies can prioritize their log monitoring efforts by focusing on the most critical systems and applications. This can help them identify and address potential threats more efficiently, reducing costs and increasing the overall effectiveness of monitoring.
Regular testing: Regularly testing and evaluating log monitoring systems can help companies identify potential vulnerabilities and improve their overall security posture. By testing their systems, companies can also ensure that they are able to detect and respond to potential threats effectively.
Outsourcing: Companies can also consider outsourcing log monitoring and analysis to a third-party vendor. This can help them reduce costs associated with hiring and training employees, and also provide them access to specialized expertise and resources.
In addition, companies can also incorporate security ISO and NIST standards into their security log monitoring and response strategy to ensure they are doing it in a cost-effective manner while also staying compliant with the regulations. This will help them manage risks and remain protected from cyber threats.
Remember: regular security log monitoring and response is a critical component of any cybersecurity strategy. By detecting and responding to potential threats quickly and effectively, organizations can prevent significant damage and meet compliance requirements. With the increasing number of cyber threats and data breaches, it is essential for organizations to prioritize regular security log monitoring and response to protect their sensitive information and assets.
5 Ways to Motivate Your Cybersecurity Team to Take Network Security Seriously

As a cybersecurity professional, you know how important it is to protect your organization’s networks and data. But even the most skilled and dedicated cybersecurity personnel can get complacent or burnt out over time. So, how do you keep your team motivated and engaged in the critical task of safeguarding your network? Here are five strategies that can help:
- Make security personal: One of the most effective ways to motivate people is to make the issue relevant to their own lives. When it comes to cybersecurity, this means showing team members how a breach could impact them personally, such as by exposing their personal information or damaging their reputation. You could also share real-life examples of how other organizations or individuals have suffered from cyber attacks.
- Emphasize the impact on the organization: Another way to motivate your team is to highlight the consequences of a security breach for the organization as a whole. This could include financial losses, legal liabilities, damage to the organization’s reputation, and other negative outcomes. By emphasizing the bigger picture, you can help your team see the value of their work and the importance of being vigilant.
- Foster a culture of security: A strong culture of security can go a long way in keeping your team motivated. This means establishing clear security policies and procedures, providing ongoing training and resources, and rewarding team members for their contributions to security. You could also create a sense of camaraderie and shared responsibility by forming a security task force or holding regular security drills.
- Offer incentives and rewards: People are often more motivated when they have something to gain. You could consider offering incentives and rewards for good security practices, such as gift cards, time off, or other perks. You could also recognize and celebrate the achievements of team members who go above and beyond in protecting the network.
- Provide support and recognition: Finally, it’s important to show your team that their work is valued and appreciated. This could include providing support for professional development, offering praise and recognition for a job well done, and making sure team members have the resources and tools they need to succeed. By showing your team that you care about their well-being and success, you can help keep them motivated and engaged in their work.
By following these strategies, you can help your cybersecurity team stay motivated and committed to protecting your organization’s networks and data. As a result, you’ll not only improve security, but also build a stronger, more cohesive team.
WatchDog Case #2: Breach Prevention with Continuous Log Monitoring
ACME Corporation (fictitious name) is a leading provider of cloud-based software solutions for small and medium-sized businesses. In 2021, the company experienced a cyber breach that exposed the personal data of millions of its customers. The breach occurred when a hacker gained access to ACME’s network by using an employee’s stolen credentials.

The hacker was able to go undetected for several months, during which time they exfiltrated a large amount of sensitive data. It wasn’t until ACME’s customers began reporting suspicious activity on their accounts that the company realized something was wrong. By then, it was too late. The damage had been done, and ACME’s reputation was severely damaged as a result.
Upon further investigation, it was discovered that the hacker had accessed the network using a compromised employee’s login credentials. This employee had fallen victim to a phishing attack and had unknowingly provided the hacker with access to the company’s network.
If ACME had been utilizing continuous log monitoring, the breach may have been prevented. Continuous log monitoring involves the continuous collection and analysis of log data from various systems and devices within a network. By analyzing this log data in real-time, security teams can detect anomalies and suspicious activity that may indicate a cyber attack.
In the case of ACME, continuous log monitoring would have alerted the security team to the fact that an unauthorized user was accessing the network using an employee’s credentials. The team could then have taken immediate action to investigate and stop the attack before it caused any harm.
Continuous log monitoring can also help organizations to comply with various regulations and standards, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). These regulations require companies to implement robust security measures to protect sensitive data, and continuous log monitoring is an essential component of a comprehensive security strategy.
The lesson learned is that ACME Corporation’s cyber breach could have been prevented with the use of continuous log monitoring. By continuously collecting and analyzing log data, security teams can detect and respond to potential threats in real-time, protecting the organization and its customers from harm. Investing in continuous log monitoring is not only essential for protecting against cyber attacks, but it also helps organizations to comply with industry regulations and standards.
Future Gen gets approved for CyberSecurity services
PH Elections, Manila Bulletin and Dashboards
Here is a sample map of mock data from the Comelec’s transparency server and working with Manila Bulletin newspaper.

Google Trends PH Pres Search
Real Time Updates of Google Search Trends for PH Presidential Candidates, using Worldwide Scope and the most recent 7 days’ data.
In Demand Jobs to Enhance Your Wellbeing and Succeed During COVID-19
Having work-life balance is vital to achieving happiness in life. In the US, most employees spend over 40 hours per week at work. Overwork can have adverse effects on your health. So, even if you have a six-figure salary, you must recognize when it’s time to take a break. Because of COVID-19, companies have experienced a shortage of talent. They are now offering exceptional salaries and perks to attract the attention of qualified candidates.
Because of the increasing demand for tech skills, the competition has become tougher. Many workers are jobless because of the pandemic, and they are struggling to get a new job. If you’re wondering how to succeed during COVID-19, here are some job alternatives that will help you become an attractive worker. As you’ll have what’s necessary to meet world-class companies’ requirements, getting employed and having a better lifestyle won’t be a barrier.
Digital Marketer

The coronavirus pandemic accelerated the pace of the digital transition. Digital channels have become mainstream, and companies are looking for new ways to attract customers’ attention. Nowadays, digital marketers play a crucial role in improving companies’ marketing strategies and increasing brand recognition. Digital marketers use websites, social networks, and email to provide the best customer service.
Years ago, using television, radio, and newspapers was an excellent option to attract and retain customers. But, since they are spending more online, digital advertising plays an essential role in making customers feel engaged. You need to learn a wide range of tech skills to become a digital marketer. However, Thinkful is a coding school that makes becoming a digital marketer much easier.
Thinkful is committed to its students’ success. For that reason, students receive help from a career coach, an industry-experienced mentor, and an academic success manager throughout each course. Their tuition guarantee allows students to receive their money back if they don’t land a qualifying job within six months of graduation.
At Thinkful, students learn everything they need to stand out from the competition. In that case, landing the job of your dreams will be possible. For example, a digital marketer can earn, on average, $120K per year at Amazon. They can also enjoy great perks like paid time off, annual discounts, and paid parental leave.
Mobile Developer

Mobile apps are helping companies reshape the market. They provide customers with the power to control everything with only one tool. Smartphones have become essential for our everyday lives, and companies are using mobile apps to make them more comfortable. Since online shopping is what customers prefer, companies like Home Depot and Gucci have taken their apps to the next level. By implementing augmented reality features, their apps allow customers to have 3D previews of products.
Gucci’s app enables users to try on shoes before they buy them by using their smartphones’ cameras. Home Depot provides users with 3D previews of merchandise. With this technology, customers can see how products fit in a specific room. AR has allowed organizations to provide a better user experience and reduce costs on product returns.
In 2020, companies like Apple and Samsung are providing mobile developers with benefits and perks like on-site gym classes and spa sessions. Also, workers can receive product discounts and even tuition reimbursement benefits. Professional development has become a need, and companies are willing to do everything they can to meet the needs of skilled aspirants.
You can take online courses or enroll in a coding bootcamp like General Assembly to learn mobile development skills. General Assembly offers not only an iOS development course but also an Android development course. In that case, aspirants can decide between learning Java or Swift skills.
At General Assembly, students learn from experience by building real mobile apps. They get the right knowledge to design and code any app. Also, they gain an understanding of fundamental concepts to impress employers during interviews.
Cybersecurity Specialist

Since data is helping companies take significant strides, cybersecurity specialists have become a must for organizations. These professionals are responsible for keeping companies’ data safe and improving security strategies. Cybersecurity experts have to search for vulnerabilities in software and hardware. And by implementing analytics skills, they must develop new strategies to deal with potential threats.
Since they have a lot of responsibilities on their shoulders, more companies are providing outstanding benefits. They can work from home and enjoy schedule flexibility. Also, organizations like Microsoft provide workers with health insurance benefits and premium savings to help them improve their wellness. Becoming a cybersecurity expert requires a lot of tenacity. But, I can assure you that your efforts will be rewarded.
Flatiron School offers a cybersecurity program that allows aspirants to learn how to deal with rapidly-advancing threats. With their real-world lab environments, students can learn how to set traps and catch hackers. The program is offered full-time and can be completed in only 12 weeks.
Data Scientist

Becoming a data scientist is an excellent alternative to enhance your wellbeing and succeed during COVID-19. They are in-demand, and employers are in a hunt for candidates with data science skills. Data scientists have to analyze, interpret, and visualize data to create actionable insights. By allowing organizations to make data-driven decisions, they play a key role in leading companies to success.
Metis is a coding school that offers online education to accelerate data science learning. Their data science bootcamp is designed to give aspirants the skills and connections they need to launch a rewarding career in data science. The company counts with career advisors that help students and grads to get hired. At Metis, students learn through hands-on projects and from the best tutors.
Conclusion
In general, these job alternatives are excellent for succeeding during the pandemic. Since candidates with these kinds of skills are in-demand, getting a better job and enhancing your wellbeing won’t be a problem. No matter what option you choose, you’ll be ready to overcome unemployment as well as future challenges. Keep in mind that the tech market is a fast-growing industry and it’s affecting every industry around the globe.

