Watchdog dashboard shows that for the last 7 days ended Nov 6, 2022, attacks using port 5432 have increased by 158% (as seen below). We have sent abuse alerts to the top networks where the attacks came from. In the chart below: Incrediserve LTD network is the most prolific source of attacks (5276 incidents representing a 1,470% increase over the prior 7 days).
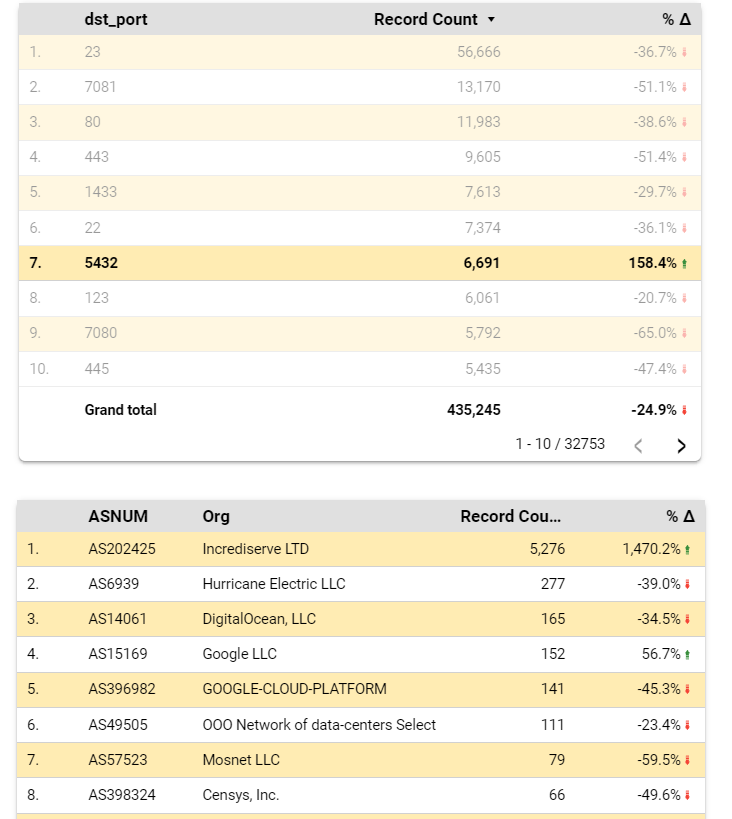
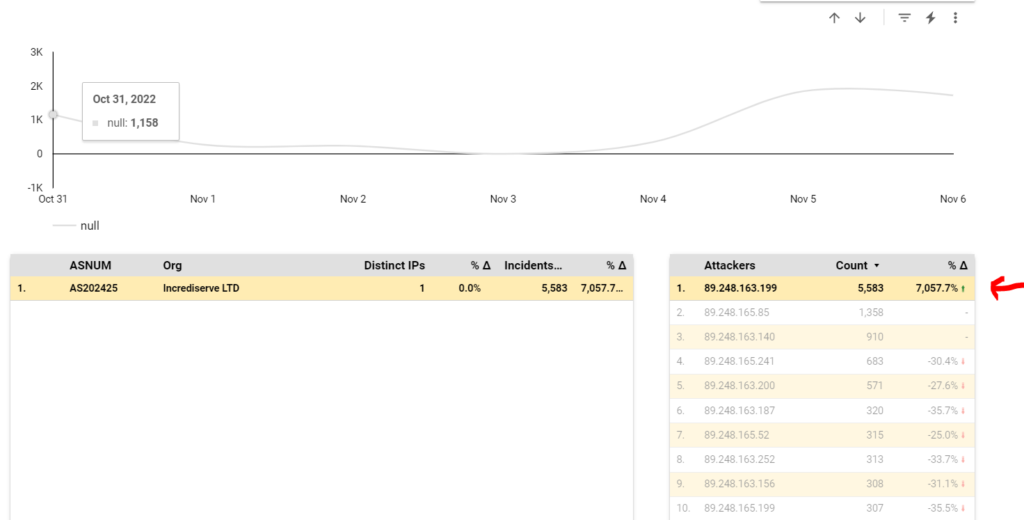
We quickly identify the rogue source IP from Incrediserve LTD using Port 5432: (In this case: 89.248.163.199). We also note the increase in attacks by this IP over the last 7 days.
What exploits are on port 5432 ?
A quick check over at SANS Internet Storm center shows that this port is associated with PostGres database server. Apple also uses this for ARD 2.0 Database.
When we compare our dashboard results with worldwide stats, there is a slight increase in world wide attacks on PostGres. This typically means that there are exploitable vulnerabilities that may or may not be patched:
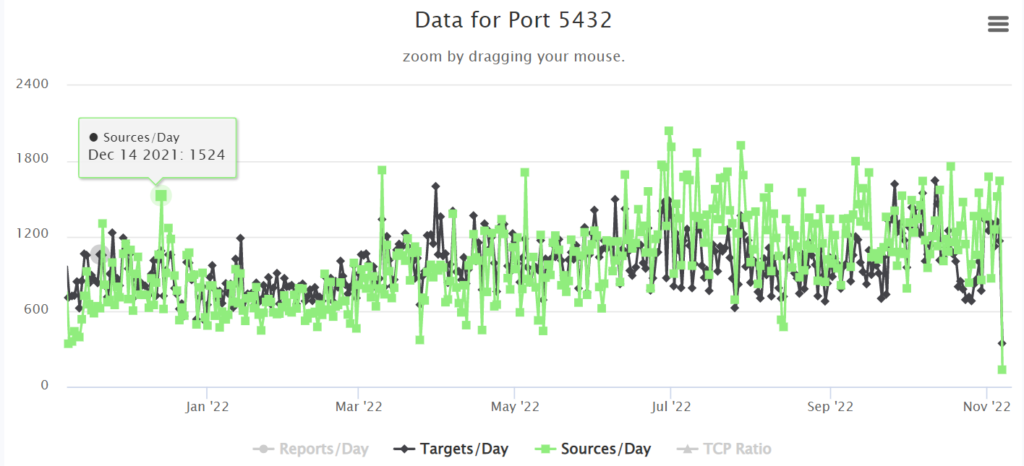
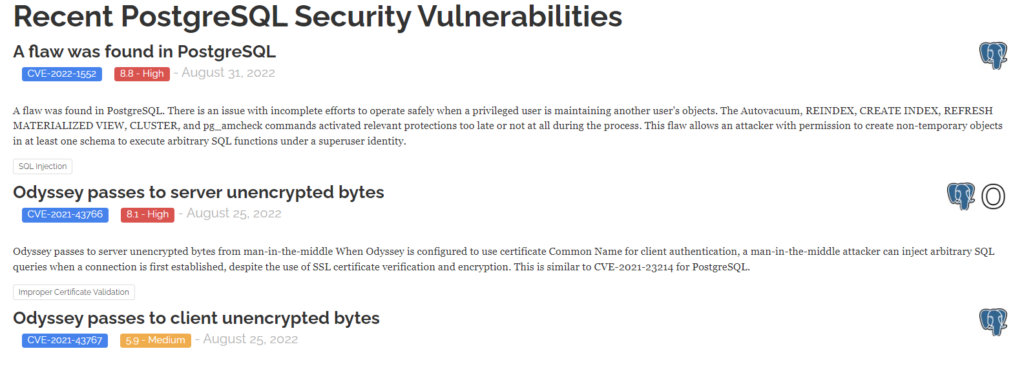
True enough. There ARE recently published vulnerabilities for PostGres (https://stack.watch/product/postgresql/)
Lesson Learned?
By monitoring our network for changes in attack patterns, we can focus on vulnerabilities that are actively being targeted. Patch your PostGres now.
To learn more about Watchdog, visit this : https://futuregen.sg/big-data/whitepaper-reducing-cyber-incidents-by-combatting-hackers-with-legal-revocation-strategy/
