
Network Monitoring: Enhancing Cyber Security Operations
In today’s digital landscape, where cyber threats continue to proliferate, ensuring robust security measures is crucial for businesses of all sizes. Cybersecurity operations play a pivotal role in safeguarding sensitive data, mitigating risks, and protecting against potential breaches.
While many organizations focus on implementing firewalls, encryption, and other security measures, one vital but often overlooked step in comprehensive cyber defense is network monitoring. In this article, we delve into the importance of network monitoring in cyber security operations and how it can significantly enhance your organization’s overall security posture.
Understanding Network Monitoring
Network monitoring involves the continuous surveillance of a computer network to identify and respond to security threats, performance issues, and other network-related problems. It provides valuable insights into the overall health, performance, and security of your network infrastructure. By leveraging advanced monitoring tools and technologies, organizations can gain real-time visibility into network activities, identify anomalies, and respond promptly to potential security breaches.
The Vital Role of Network Monitoring in Cyber Security Operations
- Proactive Threat Detection: Network monitoring acts as a proactive defense mechanism, allowing organizations to identify potential threats before they escalate into major security incidents. By monitoring network traffic, suspicious activities, and system logs, IT teams can swiftly detect unauthorized access attempts, malware infections, and other malicious activities. Early detection enables timely response, minimizing the impact of security breaches and preventing sensitive data from falling into the wrong hands.
- Improved Incident Response: In the event of a security incident, network monitoring provides essential data for incident response and forensic investigations. Detailed logs and network activity records enable IT teams to trace the source of the breach, analyze the extent of the damage, and develop effective remediation strategies. This valuable information ensures a more efficient incident response process, reducing downtime and minimizing the potential damage caused by cyber attacks.
- Enhanced Performance Optimization: Network monitoring not only aids in identifying security threats but also offers insights into network performance. By monitoring bandwidth usage, latency, and other network metrics, organizations can optimize their network infrastructure for better performance. Identifying bottlenecks, optimizing traffic flow, and managing network congestion become easier with the continuous monitoring and analysis of network data.
- Compliance and Regulatory Requirements: Many industries are subject to stringent compliance and regulatory standards regarding data privacy and security. Network monitoring plays a vital role in meeting these requirements. By monitoring network activity, organizations can ensure compliance with data protection regulations, identify vulnerabilities, and implement necessary security controls. This proactive approach helps organizations avoid penalties, legal consequences, and reputational damage associated with non-compliance.
- Internal Threat Detection: While external cyber threats are a significant concern, internal threats can also pose a substantial risk to an organization’s security. Network monitoring enables the identification of suspicious activities originating from within the network, such as insider threats or unauthorized access attempts by employees. By monitoring user behavior, access privileges, and data transfers, organizations can detect and mitigate internal security risks more effectively.
Best Practices for Effective Network Monitoring
To harness the full potential of network monitoring, organizations should consider the following best practices:
- Choose the Right Tools: Invest in robust network monitoring tools capable of providing real-time insights into network activities, identifying anomalies, and generating actionable alerts. Select tools that align with your organization’s specific needs and network infrastructure.
- Implement Comprehensive Monitoring: Monitor all critical network components, including routers, switches, firewalls, servers, and endpoints. Ensure that network monitoring covers both internal and external network traffic to gain a holistic view of your organization’s security landscape.
- Continuous Monitoring and Analysis: Network monitoring should be an ongoing process, not a one-time setup. Regularly review network logs, conduct deep packet inspections, and analyze network traffic to identify any
- Outsource the manual portion to WatchDog. Just provide the logs and we do the rest.
The Power of Website Security: Safeguarding Your Online Presence
In today’s digital age, where online interactions have become an integral part of our daily lives, ensuring the security of your website has never been more crucial. Cyber threats and attacks are on the rise, putting sensitive data, user privacy, and even business reputation at risk. As a leading provider of website security solutions, we understand the importance of safeguarding your online presence. In this article, we delve into the realm of website security, offering valuable insights and practical steps to help you fortify your website against potential vulnerabilities and outrank other websites in Google search results.
The Rising Threat Landscape
Cybercriminals are becoming increasingly sophisticated in their methods, constantly seeking new ways to exploit weaknesses in websites. From data breaches and malware infections to hacking attempts and distributed denial-of-service (DDoS) attacks, the threat landscape is diverse and ever-evolving. It is imperative for website owners to adopt a proactive approach to protect their digital assets.
Understanding Website Vulnerabilities
Before we delve into effective security strategies, it is essential to understand the common vulnerabilities that can be exploited by malicious actors. By gaining insights into these weak points, you can take appropriate measures to mitigate potential risks. Here are a few noteworthy vulnerabilities:
1. Outdated Software and Plugins
Running outdated versions of content management systems (CMS) or using obsolete plugins can open doors for cyber attackers. These outdated components often have known vulnerabilities that can be easily exploited.
2. Weak Authentication Mechanisms
Weak passwords, default login credentials, or lack of two-factor authentication (2FA) can leave your website susceptible to brute-force attacks or unauthorized access attempts.
3. Insecure Communication Channels
Failure to implement secure communication protocols, such as SSL/TLS, can expose sensitive data to eavesdropping or interception by malicious individuals.
4. Cross-Site Scripting (XSS)
XSS attacks occur when an attacker injects malicious code into a website, which then gets executed by unsuspecting users’ browsers, potentially compromising their data or exposing them to further attacks.
5. SQL Injection
SQL injection attacks exploit vulnerabilities in web applications that do not properly validate user input. Attackers can manipulate database queries, potentially gaining unauthorized access to sensitive information or modifying data.
Effective Strategies for Website Security
To outrank other websites and establish your online presence as a reliable and secure destination, it is crucial to implement robust security measures. Below, we outline key strategies that will help safeguard your website:
1. Regular Software Updates and Patching
Keeping your CMS, plugins, and other software components up to date is paramount. Developers frequently release security patches and bug fixes to address vulnerabilities. Staying current with these updates is vital to ensure your website remains secure.
2. Strong Authentication Practices
Implementing strong passwords, enforcing password complexity rules, and encouraging the use of 2FA significantly enhance your website’s security posture. By adding an additional layer of verification, you mitigate the risk of unauthorized access.
3. SSL/TLS Encryption
Securing your website with SSL/TLS certificates ensures that data transmitted between your users and the server remains encrypted and cannot be easily intercepted or tampered with. This fosters trust among visitors and can positively impact your search engine rankings.
4. Web Application Firewalls (WAF)
Deploying a WAF helps protect your website against common vulnerabilities, such as XSS and SQL injection. It acts as a shield, analyzing incoming traffic and filtering out potentially malicious requests, ensuring the integrity of your website’s data.
5. Continuous Security Monitoring
Utilize robust security monitoring tools to detect and respond to potential threats in real-time. Implementing intrusion detection systems (IDS)
Cost-Effective Strategies for Log Monitoring and Response: How to Keep Your Company Safe from Cyber Threats
As the world becomes increasingly digitized and connected, the importance of regular security log monitoring and response cannot be overstated. In today’s digital age, cyber threats are a constant and growing concern:
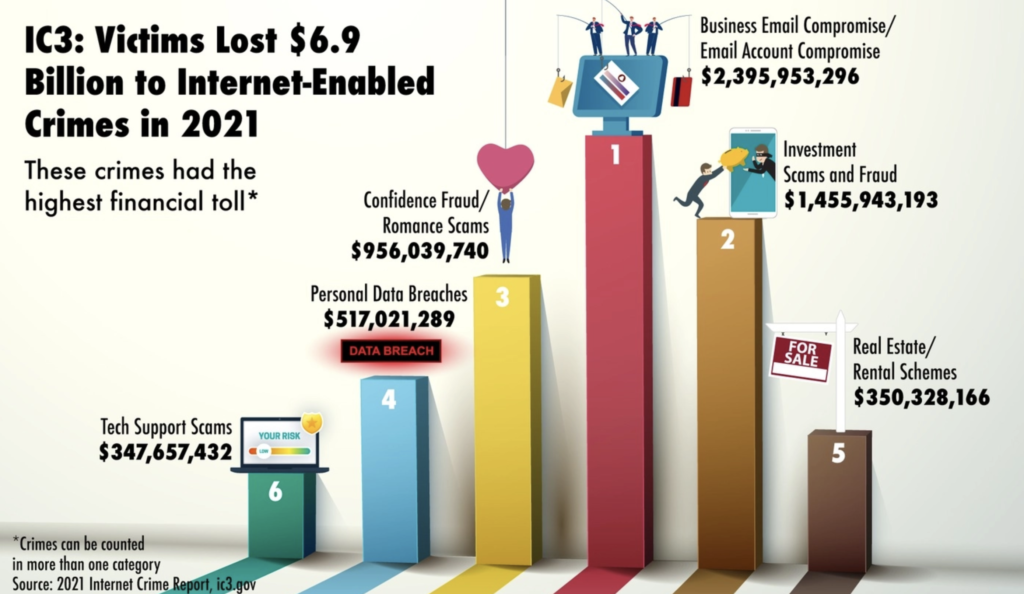
It is essential to have a proactive and comprehensive approach to security. Regular security log monitoring and response is an essential part of any cybersecurity strategy.
One of the key benefits of regular security log monitoring and response is that it allows organizations to detect and respond to potential threats quickly and effectively. By constantly monitoring logs and identifying patterns and anomalies, security teams can quickly identify and respond to potential threats, preventing them from causing significant damage.
According to a study by the Ponemon Institute, organizations that have a strong security incident response plan are able to detect and contain breaches in an average of 46 days, compared to an average of 201 days for organizations without a plan.
Another key benefit of regular security log monitoring and response is that it helps organizations meet compliance requirements. Standards such as ISO 27001 and NIST SP 800-53 require organizations to have a comprehensive security management system that includes regular security log monitoring and response. By implementing these standards, organizations can demonstrate to customers, partners, and regulators that they have taken the necessary steps to protect sensitive data and prevent breaches.
Case studies also demonstrate the value of regular security log monitoring and response:
For example, in 2016, a major healthcare organization experienced a data breach that exposed the personal information of nearly 4 million patients. The cause of the breach was a failure to monitor security logs, which would have revealed suspicious activity and allowed the organization to take action before the breach occurred. This incident highlights the importance of regular security log monitoring and response and the potential consequences of not having it in place.
Companies can do log monitoring in a cost-effective manner by implementing the following strategies:
Automation: Automating log monitoring and analysis can significantly reduce the cost of manual monitoring and analysis. By using automated tools, companies can analyze and identify potential threats in real-time, without the need for manual intervention. This can significantly reduce labor costs and increase the effectiveness of monitoring.
Cloud-based solutions: Utilizing cloud-based log monitoring solutions can help companies reduce the costs associated with maintaining and scaling their own infrastructure. Cloud-based solutions also offer automatic updates, eliminating the need for additional costs to maintain software.
Prioritization: Companies can prioritize their log monitoring efforts by focusing on the most critical systems and applications. This can help them identify and address potential threats more efficiently, reducing costs and increasing the overall effectiveness of monitoring.
Regular testing: Regularly testing and evaluating log monitoring systems can help companies identify potential vulnerabilities and improve their overall security posture. By testing their systems, companies can also ensure that they are able to detect and respond to potential threats effectively.
Outsourcing: Companies can also consider outsourcing log monitoring and analysis to a third-party vendor. This can help them reduce costs associated with hiring and training employees, and also provide them access to specialized expertise and resources.
In addition, companies can also incorporate security ISO and NIST standards into their security log monitoring and response strategy to ensure they are doing it in a cost-effective manner while also staying compliant with the regulations. This will help them manage risks and remain protected from cyber threats.
Remember: regular security log monitoring and response is a critical component of any cybersecurity strategy. By detecting and responding to potential threats quickly and effectively, organizations can prevent significant damage and meet compliance requirements. With the increasing number of cyber threats and data breaches, it is essential for organizations to prioritize regular security log monitoring and response to protect their sensitive information and assets.
5 Ways to Motivate Your Cybersecurity Team to Take Network Security Seriously

As a cybersecurity professional, you know how important it is to protect your organization’s networks and data. But even the most skilled and dedicated cybersecurity personnel can get complacent or burnt out over time. So, how do you keep your team motivated and engaged in the critical task of safeguarding your network? Here are five strategies that can help:
- Make security personal: One of the most effective ways to motivate people is to make the issue relevant to their own lives. When it comes to cybersecurity, this means showing team members how a breach could impact them personally, such as by exposing their personal information or damaging their reputation. You could also share real-life examples of how other organizations or individuals have suffered from cyber attacks.
- Emphasize the impact on the organization: Another way to motivate your team is to highlight the consequences of a security breach for the organization as a whole. This could include financial losses, legal liabilities, damage to the organization’s reputation, and other negative outcomes. By emphasizing the bigger picture, you can help your team see the value of their work and the importance of being vigilant.
- Foster a culture of security: A strong culture of security can go a long way in keeping your team motivated. This means establishing clear security policies and procedures, providing ongoing training and resources, and rewarding team members for their contributions to security. You could also create a sense of camaraderie and shared responsibility by forming a security task force or holding regular security drills.
- Offer incentives and rewards: People are often more motivated when they have something to gain. You could consider offering incentives and rewards for good security practices, such as gift cards, time off, or other perks. You could also recognize and celebrate the achievements of team members who go above and beyond in protecting the network.
- Provide support and recognition: Finally, it’s important to show your team that their work is valued and appreciated. This could include providing support for professional development, offering praise and recognition for a job well done, and making sure team members have the resources and tools they need to succeed. By showing your team that you care about their well-being and success, you can help keep them motivated and engaged in their work.
By following these strategies, you can help your cybersecurity team stay motivated and committed to protecting your organization’s networks and data. As a result, you’ll not only improve security, but also build a stronger, more cohesive team.
WatchDog Case #2: Breach Prevention with Continuous Log Monitoring
ACME Corporation (fictitious name) is a leading provider of cloud-based software solutions for small and medium-sized businesses. In 2021, the company experienced a cyber breach that exposed the personal data of millions of its customers. The breach occurred when a hacker gained access to ACME’s network by using an employee’s stolen credentials.

The hacker was able to go undetected for several months, during which time they exfiltrated a large amount of sensitive data. It wasn’t until ACME’s customers began reporting suspicious activity on their accounts that the company realized something was wrong. By then, it was too late. The damage had been done, and ACME’s reputation was severely damaged as a result.
Upon further investigation, it was discovered that the hacker had accessed the network using a compromised employee’s login credentials. This employee had fallen victim to a phishing attack and had unknowingly provided the hacker with access to the company’s network.
If ACME had been utilizing continuous log monitoring, the breach may have been prevented. Continuous log monitoring involves the continuous collection and analysis of log data from various systems and devices within a network. By analyzing this log data in real-time, security teams can detect anomalies and suspicious activity that may indicate a cyber attack.
In the case of ACME, continuous log monitoring would have alerted the security team to the fact that an unauthorized user was accessing the network using an employee’s credentials. The team could then have taken immediate action to investigate and stop the attack before it caused any harm.
Continuous log monitoring can also help organizations to comply with various regulations and standards, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). These regulations require companies to implement robust security measures to protect sensitive data, and continuous log monitoring is an essential component of a comprehensive security strategy.
The lesson learned is that ACME Corporation’s cyber breach could have been prevented with the use of continuous log monitoring. By continuously collecting and analyzing log data, security teams can detect and respond to potential threats in real-time, protecting the organization and its customers from harm. Investing in continuous log monitoring is not only essential for protecting against cyber attacks, but it also helps organizations to comply with industry regulations and standards.
WatchDog Case 1: Attacks on Port 5432
Watchdog dashboard shows that for the last 7 days ended Nov 6, 2022, attacks using port 5432 have increased by 158% (as seen below). We have sent abuse alerts to the top networks where the attacks came from. In the chart below: Incrediserve LTD network is the most prolific source of attacks (5276 incidents representing a 1,470% increase over the prior 7 days).
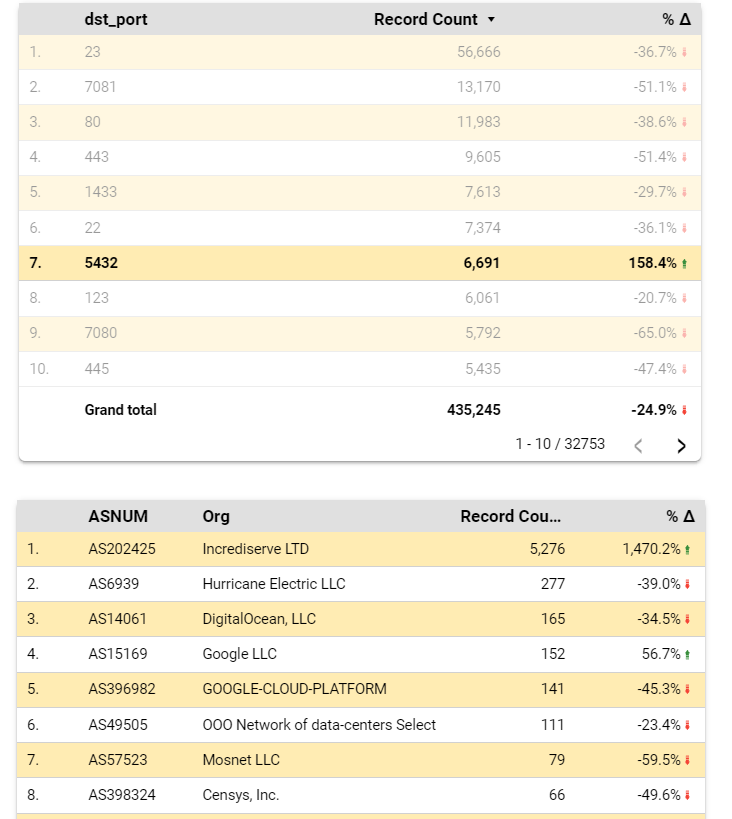
We quickly identify the rogue source IP from Incrediserve LTD using Port 5432: (In this case: 89.248.163.199). We also note the increase in attacks by this IP over the last 7 days.
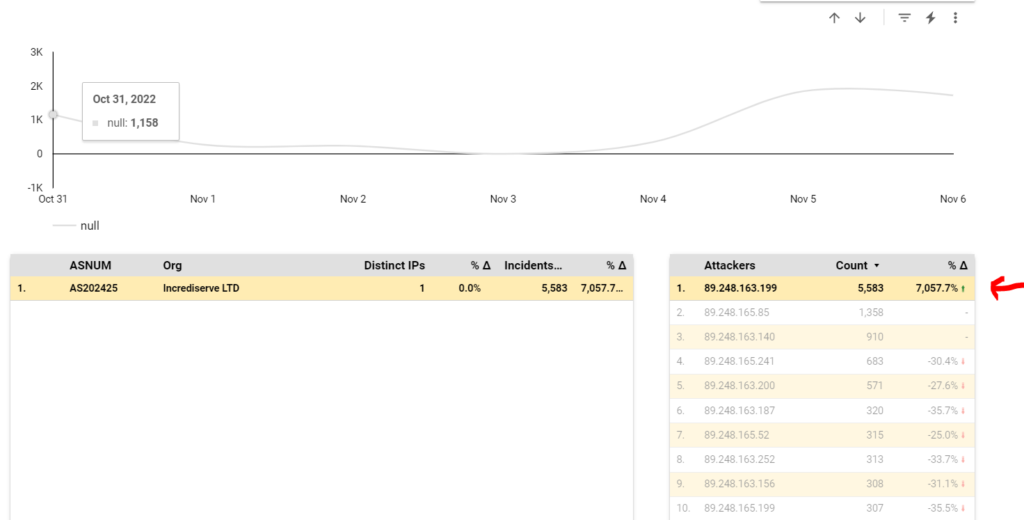
What exploits are on port 5432 ?
A quick check over at SANS Internet Storm center shows that this port is associated with PostGres database server. Apple also uses this for ARD 2.0 Database.
When we compare our dashboard results with worldwide stats, there is a slight increase in world wide attacks on PostGres. This typically means that there are exploitable vulnerabilities that may or may not be patched:
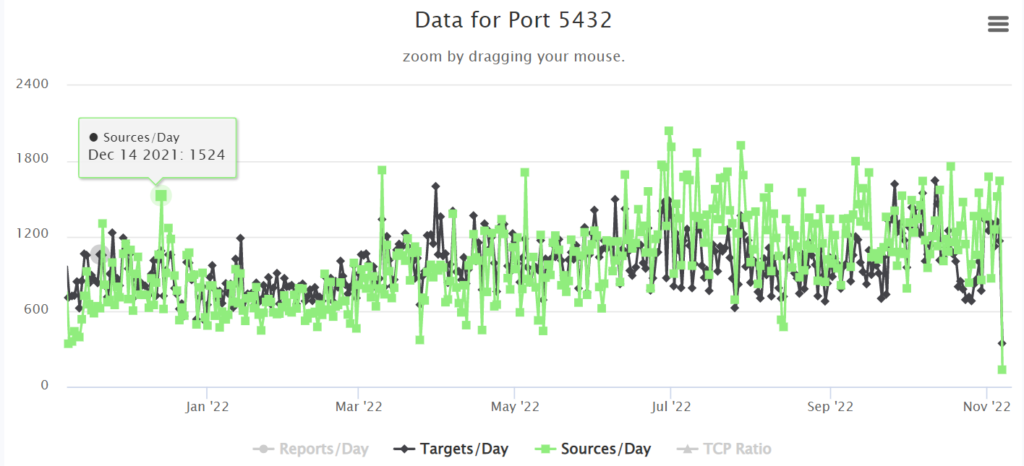
True enough. There ARE recently published vulnerabilities for PostGres (https://stack.watch/product/postgresql/)
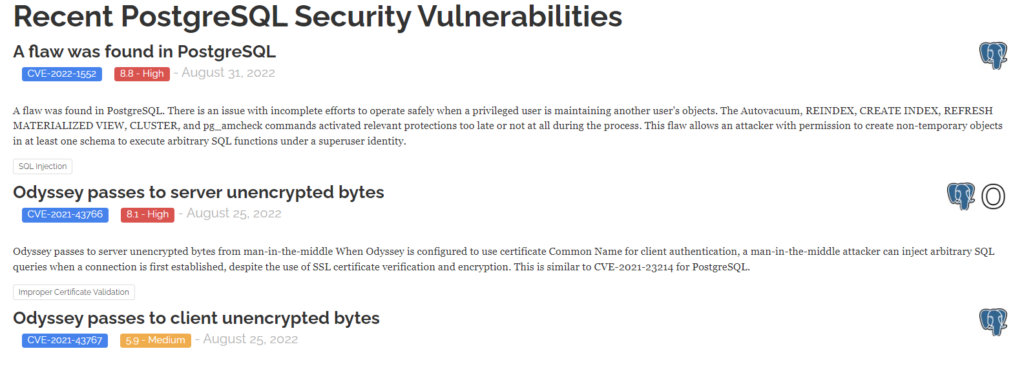
Lesson Learned?
By monitoring our network for changes in attack patterns, we can focus on vulnerabilities that are actively being targeted. Patch your PostGres now.
To learn more about Watchdog, visit this : https://futuregen.sg/big-data/whitepaper-reducing-cyber-incidents-by-combatting-hackers-with-legal-revocation-strategy/
Whitepaper: Reducing Cyber Incidents by combatting hackers with Legal Revocation Strategy
Detering Hackers
Hacking is prevalent because of the asymmetrical relationship between cost and reward to the hacker. On average, a hacker reaps US$9.2 while expending little effort or resources. Meanwhile, the company suffers US$9.2M in total damages; this excludes IT and legal costs, ransoms, and reputation.
A company’s defense consists of patching known vulnerabilities while the IT Department focuses on ongoing business operations. Coupled with the prevalent business view that breaches are a cost of doing business rather than a critical threat, cyber breaches thrive in this organizational climate.
Watchdog provides a systematic method to remove hackers’ internet access and compromised resources through legal means while preserving the evidence for legal actions.
Data Security Matters:
With the average cyber breach costing $9.2 million dollars per incident, governments are increasingly holding corporations accountable for basic cyber security. Fully 72% of network breaches are conducted by opportunistic hackers without a focused target. These involve lesser secured networks instead of attacking more secure networks.
By increasing network security and pushing back against hackers, an organization can decrease attacks, preserve forensic evidence, and automate government-mandated compliance reporting.
The data breach results from a multi-stage process known as a “cyber kill chain”. These may take weeks or months to complete and is dependent on the previous stages being uninterrupted.
Automated breach detection and revocation of a hacker’s resources lowers the attack’s frequency and reduces the chances of an attack becoming successful. Halting the process earlier in the kill chain generally results in lesser damages and liabilities.
The Kill Chain (What Hackers Do)
A successful breach requires the sequentially dependent steps to be undetected and unremoved.
- Reconnaissance – gathering social or technical information to prepare for the attack
- Weaponization – creating malware to exploit the discovered backdoors
- Delivery – delivering the malware for future execution
- Exploitation – activating the previously delivered malware
- Installation – installing additional malware
- Command and Control – enabling remote control of discovered assets
- Action – extracting, encryption, or deleting of the critical assets
Watchdog Active Countermeasures
By imposing a noticeable cost to hackers, legal active countermeasures can deter most attempts to establish a kill chain in a network, thus preventing future breaches. Hackers avoid networks that are expensive to exploit.
Watchdog’s active countermeasures consist of:
- Analyzing network activity logs with our artificial intelligence to detect malicious activities.
- Sending revocation requests to the ISP’s and companies where the threat activity originated from.
- Maintaining a database of threat activity records as time-stamped evidence for use by your legal department if it is ever needed.
Why are Active Countermeasures effective?
Implementing active countermeasures is an effective deterrent because of:
- Decreased Breach Exposure. The majority of breach exposures are exploited because of misconfigured network settings, protocols, or unintentional interaction of different service services. Detecting low-level breaches and sending out revocation requests will undermine the hacker’s resources. This makes your network more secure and lessens a hacker’s inclination to attack a network that rapidly decreases known vulnerabilities.
- Automated Mitigation. Alerting Internet Service Providers to possible compromises on their network will lead them to stop the rogue processes or suspend user accounts in most cases. They will effectively be assisting you in protecting your network from bad actors by denying them “safe harbor” on the networks where they launch their attacks from.
- Focused Organizational Resources. Watchdog analyzes web activities and sends out alerts. This will allow your team to focus on the most critical attacks. Your team focuses on end-stage breaches to prevent a devastating hack.
Can’t do it? Let Watchdog do it for you!
While Offense gets the glory, it is DEFENSE that wins the Game! Beef up your defensive strategies with Watchdog.
Watchdog will take your router, firewall, and server weblogs, then analyze them with our artificial intelligence application that is monitored by a certified cybersecurity team housed in our Singapore-licensed security operations center (SOC).
Watchdog will enhance your raw logs with other annotated data to create revocation requests that are automatically sent by e-mail to the ISP’s and companies where the threat activity originated from.
Finally, Watchdog will archive all the log records as integrated, time-stamped evidence for your legal department.
Enroll in our free pilot to demonstrate the benefits (US$10,800 value)
For a limited time, we are offering qualified companies a FREE 30-day Trial of Watchdog cyber monitoring and alert service, valued at US$10,800 annually.
Click < HERE > to avail of this FREE Trial subscription.
Future Gen gets approved for CyberSecurity services
PH Elections, Manila Bulletin and Dashboards
Here is a sample map of mock data from the Comelec’s transparency server and working with Manila Bulletin newspaper.


